Slow Liquidity Drains (SLID) are rapidly emerging as one of the most insidious threats facing decentralized finance. Unlike high-profile rug pulls or flash loan exploits, SLID schemes operate beneath the surface, quietly siphoning funds from liquidity pools over extended periods. This gradual depletion is not just a technical curiosity – it poses a systemic risk to protocol stability and user capital, as demonstrated by a comprehensive study of 319,166 liquidity pools across six major decentralized exchanges. The findings are sobering: 3,117 pools were compromised by SLID, with cumulative losses exceeding $103 million (arxiv.org).

Why SLID Is Harder to Detect Than Rug Pulls
Traditional DeFi scams like rug pulls are explosive and unmistakable – funds vanish instantly, alarms sound, and the community reacts in real time. SLID, on the other hand, is engineered for stealth. Malicious actors leverage protocol vulnerabilities or subtly manipulate pool mechanics to extract value in small increments, often over weeks or months. This methodical approach allows them to avoid triggering the typical on-chain heuristics or monitoring alerts that flag rapid outflows.
The result is a persistent erosion of liquidity that only becomes apparent when it is too late. By the time the community or protocol operators notice the drain, the attacker has already walked away with significant capital, and the pool’s health is compromised.
The Mechanics of a Slow Liquidity Drain
A SLID exploit typically starts with an attacker identifying a flaw in a protocol’s incentive structure or smart contract logic. They might:
Key Tactics in SLID DeFi Attacks and Their Distinctions
-
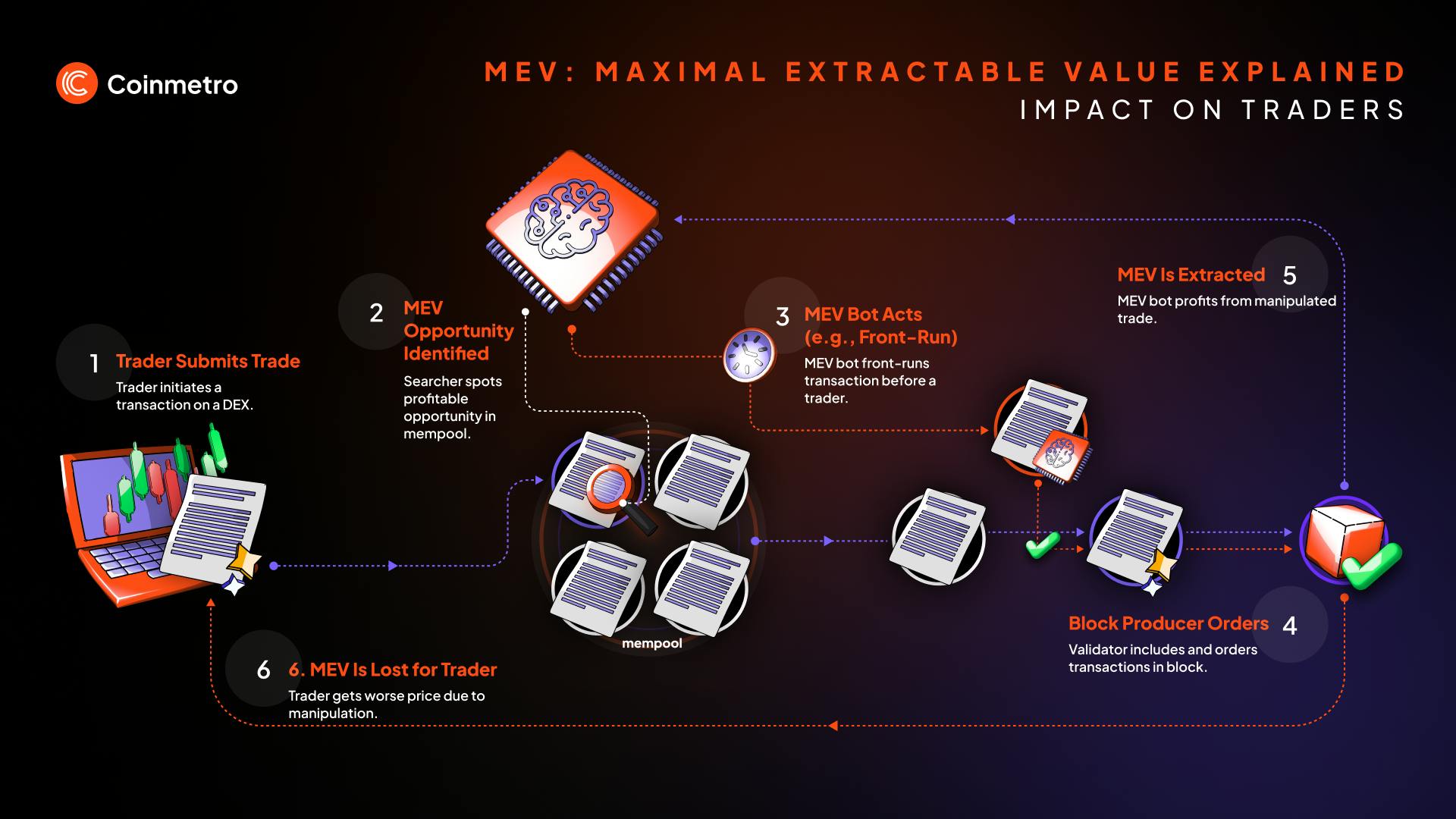
Gradual Extraction via Automated Scripts: Attackers deploy automated bots that slowly withdraw liquidity from targeted pools over weeks or months, making the drain less noticeable compared to sudden rug pulls.
-

Exploiting Protocol Logic Flaws: SLID attackers identify and exploit subtle smart contract vulnerabilities—such as rounding errors or unchecked withdrawal functions—to siphon small amounts per transaction, avoiding immediate detection.
-

Sybil Attacks with Multiple Wallets: Bad actors use many pseudonymous wallets to spread out withdrawals, mimicking normal user behavior and circumventing anti-fraud systems that might flag large, single-account drains.
-
Manipulating Pool Parameters: Attackers subtly adjust liquidity pool parameters (e.g., fee structures or weights in automated market makers) to incrementally favor their own positions, draining value over time.
-
Contrast with Flash Loan and Rug Pull Exploits: Unlike flash loan attacks (which exploit vulnerabilities in a single, rapid transaction) or rug pulls (which drain all funds instantly), SLID attacks are characterized by their slow, persistent, and stealthy approach, making them harder to detect and mitigate.
For example, an attacker may repeatedly perform small, seemingly legitimate swaps that exploit a rounding error or fee miscalculation. Alternatively, they might slowly withdraw liquidity in a way that avoids slippage thresholds or governance triggers. In aggregate, these micro-extractions can drain millions from a protocol, all while maintaining the appearance of normal activity.
Systemic Risks: How SLID Weakens DeFi Protocols and User Funds
The slow, persistent nature of SLID attacks has a compounding effect on DeFi ecosystem stability:
- Erosion of Liquidity: As funds are drained, pools become less deep, increasing slippage and reducing trading efficiency for all users.
- Loss of User Confidence: Users may not notice the drain immediately, but as yields drop and execution worsens, trust in the protocol erodes. This can trigger further withdrawals and a negative feedback loop.
- Increased Vulnerability: A weakened pool is more susceptible to additional attacks, including classic exploits or cascading liquidations caused by insufficient reserves.
This is not just theoretical. The $103 million lost to SLID so far demonstrates that these risks are material, persistent, and capable of undermining even the most established protocols if left unchecked.
How Can DeFi Users and Protocols Respond?
Given the stealthy nature of SLID attacks, traditional monitoring solutions are often inadequate. The DeFi community must adopt a multi-layered approach to detection and mitigation:
- Real-Time Analytics: Deploy advanced on-chain analytics that track not just large, sudden outflows, but also subtle, persistent patterns of liquidity movement. Machine learning models can help flag deviations from historical pool behavior, even when the changes are gradual.
- Protocol-Level Circuit Breakers: Integrate automated safeguards that pause or throttle withdrawals if anomalous patterns emerge, even if the absolute amounts are small. This can provide crucial reaction time before significant losses accrue.
- Continuous Auditing and Bounty Programs: Move beyond one-off audits by using continuous monitoring and incentivizing white-hat hackers to probe for vulnerabilities that could enable SLID-type exploits.
- User Participation in Governance: Encourage active community oversight and transparency. When users are empowered to propose and vote on risk parameters, it becomes harder for attackers to exploit overlooked vectors.
Importantly, users should not rely solely on protocol teams. Proactive self-protection includes diversifying liquidity across multiple pools, using risk hedging tools, and staying informed about emerging threats through trusted resources like DepegWatch.
Innovative Hedging Tools for SLID and Liquidity Pool Risk
The rise of SLID DeFi exploits has accelerated the development of hedging products specifically designed to protect against slow, persistent drains. These solutions include:
DeFi Insurance and Hedging Solutions for SLID Risk
-

Nexus Mutual offers Smart Contract Cover that protects users against losses from smart contract vulnerabilities, including those exploited in slow liquidity drain (SLID) scenarios. Coverage is community-assessed and claims are paid in the native NXM token.
-

InsurAce.io provides multi-chain DeFi protocol insurance covering risks such as smart contract hacks and liquidity pool exploits. Their flexible cover options can be tailored to protect against gradual fund drains affecting user deposits.
-

Unslashed Finance specializes in DeFi risk coverage including protection for liquidity providers against protocol exploits and gradual capital loss. Their insurance pools are backed by diversified capital providers and offer transparent claim processes.
-

OpenCover is an aggregator that enables users to compare and purchase DeFi insurance products from multiple providers, streamlining access to coverage for risks like SLID and liquidity pool vulnerabilities.
-

Chainproof delivers regulated smart contract insurance for institutional DeFi participants, offering coverage for losses due to smart contract failures, including those that may enable slow liquidity drains.
For instance, on-chain derivatives can allow liquidity providers to short their own pool’s token or purchase options that pay out if pool balances drop below a certain threshold. Decentralized insurance protocols are also beginning to recognize SLID as a distinct risk category, offering coverage tailored to gradual, hard-to-detect exploits.
Staying Ahead: Education and Community Vigilance
Ultimately, the best defense is a well-informed user base and an active, transparent community. SLID attacks thrive on complacency and opacity. By fostering a culture of open risk discussion, regular protocol updates, and collaborative threat hunting, DeFi protocols can make themselves far less attractive targets for slow liquidity drain schemes.
As the DeFi ecosystem matures, so do the tactics of malicious actors. The persistent, stealthy nature of slow liquidity drains demands a new standard for vigilance, transparency, and technical innovation. By combining real-time analytics, robust hedging tools, and community-driven governance, both protocols and users can mitigate systemic risk and help ensure the long-term resilience of decentralized finance.